rameshvanka
Wednesday 12 October 2022
JAVA 8 - Lambads,Streams - Very Simple Manner
Tuesday 4 October 2022
Microservices/Distributed Design Patterns
I had started posting of the microservices/Distributed design patterns.
Circuit Breaker Section:
Thursday 4 August 2022
Importance of urandom egd in containers -> java -Djava.security.egd=file:/dev/urandom Importance
In high distributed, scaled applications , One System/Server needs to connect another Downstream System/Server to establish session, certificates,
Here session/certificates are having random numbers,
Our java security pickup the random number from Linux/Window entropy pool.
What is entropy pool ?
In any server, user hits the server through keyboard some other noises, Linux server capture those noises put them into entropy pool.
EGD - Entropy Gathered Device
our java security device -> java.security.egd=file:/dev/random
java.security.egd=file:/dev/random
By default java8 and java11 this property is there in the java.security file,
If entropy pool having full entries, file:/dev/random works fine,
If entropy pool having no entries, file:/dev/random will waits for long time, it is blocking the thread, it is hitting the performance.
Solution: Always use the java.security.egd=file:/dev/urandom in PCF/Kubernets/Virtual Server.
java.security.egd=file:/dev/urandom
need to pass this argument in java argument.
If entropy pool having full entries, file:/dev/urandom works fine,
If entropy pool having no entries, file:/dev/urandom will not wait, it will genereate the random number hence it will improve the performance, no blocking of the thread.
Sunday 26 July 2020
Book Review
"Learning React A Hands-On Guide to Building Web Applications Using React and Redux by Kirupa Chinnathambi" It's very good book.It's covered react fundamental very good way.
for redux storage below link given very good
https://chriscourses.com/blog/redux - react-redux
Thursday 25 June 2020
CISCO VPN - Docker Issue
Wednesday 17 June 2020
OAUTH2
I had went krutunga restaurant in my car. In the restaurant parking person is there, I will hand over my car keys to that hotel parking person. He will park my car into parking area.
Means ?
I am delegating my access to hotel parking person to park my car.
I ( Ramesh) - Resource Owner - User Context
Hotel Parking Person - Client - Client Context
Car - Resource
In the oauth2 means having 2 contexts 1) User Context 2) Client Context don't confuse.
Oauth2 id "Delegate Access Protocol"
OAuth2 having 4 main pillars
1) End User - Resource Owner
2) Client - Web application client/ any other
3) Authorization Server
4) Resource
Difference between Password Credentials and Authorization Code ?
In Password Credentials, EndUser (Ramesh) will give his credentials to Webapp Client, then Webapp Client will talk to (EndUser Credentials + Webapp Client Credentials) to Authorization Server.
In case Authorization code,
1) EndUser (Ramesh) will not share his credentials to Webapp Client,
Instead Authorization server will give login form, Enduser will enter his credentials login form, Authorization will evaluate it.
For Authorization code example:
https://www.linkedin.com/pulse/basic-oauth2-concepts-ramesh-vankayala-ramesh-vankayala/?published=t
I will update soon with diagrams to explain this concept.
Saturday 9 May 2020
Permutations Program With Backtracking
These days in coding exams very popular. Even though you are talented, it will help sharp your skills and ask companies more salary.
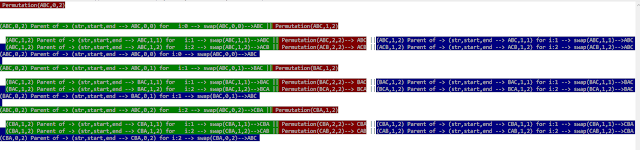
If we take the (ABC) --> How many all possible ways to combination, This problem belongs to backtracking.
Backtracking with DFS approach I had taken. DFS (Stack) - means first we will one branch we will complete that branch means here (ABC,0,0) - We will complete all possibilites then we will choose (BAC,0,1) like this way.
For this type of try to understand conceptual logic, it's very tricky here combination of for loop with recursion. for loop --> sequence, recursion --> stack (DFS)
Forumula:
Deriving the recursive with for loop forumula, I am attaching image.
p(ABC,0,2) --> for loop ( (ABC,0,0) (BAC,0,1) (CAB,0,2) )
p(ABC,1,2) --> for ( (swapped str, 1,1) (swapped str,1,2)) like this
Mixing of recursion with for loop
package optumtest.permutation;
public class PermutationTest {
public static void main(String[] args) {
String str = "ABC";
int n = str.length();
PermutationTest permutation = new PermutationTest();
permutation.permute(str, 0, n-1);
}
int ram = 0;
private void permute(String str, int start, int end) {
System.out.println("("+str+","+start+","+end+")");
if (start == end) {
System.out.println(str);
} else {
for (int i = start; i <= end; i++) {
str = swap(str, start, i);
permute(str, start + 1, end);
str = swap(str, start, i);
}
}
}
public String swap(String a, int start, int end) {
char temp;
char[] charArray = a.toCharArray();
temp = charArray[start];
charArray[start] = charArray[end];
charArray[end] = temp;
return String.valueOf(charArray);
}
}